ABSTRACT
In the last few years, the exploit of ad hoc wireless networks has increased thanks to their commercial and military potential. An application of wireless ad hoc networks is Bluetooth technology, which allows wireless communication among different devices. As a military application, we can report the establishment of communications between groups of soldiers in a not safe territory.
Additionally, ad hoc networks are useful in emergency operations, where no fixed infrastructure is feasible. A mobile ad hoc network (MANET) represents a system of wireless mobile nodes that can self-organize freely and dynamically into arbitrary and temporary network topology. On one hand, they can be quick deployed anywhere at anytime as they eliminate the complexity of infrastructure setup.
On the other hand, other problems arise, such as route errors or higher overhead, caused by the mobility of nodes. The main goal of this master’s thesis has been the improvement of the communication between MAC 802.11 protocol and DSR (Dynamic Source Routing) protocol, to run in the ns-2 network simulator.
BACKGROUND
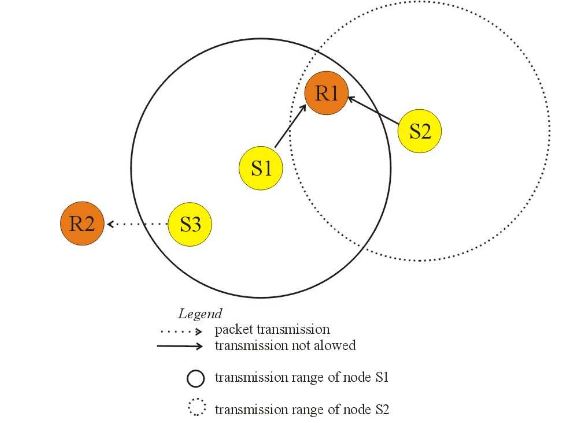
Figure 1:Hidden and exposed terminal problems
The exposed station problem happens when a node concludes mistakenly that cannot transmit, because a nearly node is transmitting to another node. Consider again figure 1, where S1 is transmitting to R1. If S3 sense the channel, it will hear an ongoing transmission, and it will falsely conclude that cannot transmit to R2. In this case, collision could happen only in the zone between S1 and R1.
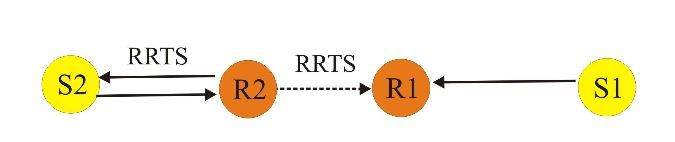
Figure 3:RRTS packet transmission
Request-for-request-to-send (RRTS) packet is used to achieve synchronization. Consider figure 3. If there is a current transmission between S1 and R1, and node, S2 wants to transmit to node R2; R1 hears CTS packets from node R1. Therefore, R1 defers its transmission. Node S2 does not know anything about the contention periods during which it can contend for the channel, and it continues trying, incrementing its backoff counter. We can solve this problem by having R2 do the contending on behalf of S2.
THE NS-2 NETWORK SIMULATOR
The use of network simulations could be understood as a cheaper way of protocol validations (both money and time), where the experimental conditions can be controlled. The last version of the network simulator, ns-2, provides many protocols like TCP, UDP or HTTP, different traffic source behaviour like CBR, FTP or VBR, propagation models, MAC layer protocols, tools for topology generation and visualization. In this master’s thesis project, we focused on MAC 802.11 implementation and DSR routing protocol.
CROSS LAYER DESIGN FOR MANET
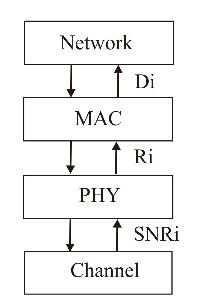
Figure 7: Cross layer communication
An example of how to improve the network throughput in wireless networks using SNR is described by Velayos & Karlsson in techniques to reduce the 802.11 handoff time, which is explained as follows. Link-layer handoff is the change of the access point (AP) to which a station is connected. However, in wireless IEEE 802.11, the handoff refers to the actions that interrupt the transmission of data, such as change of radio channel or exchange of signalling messages.
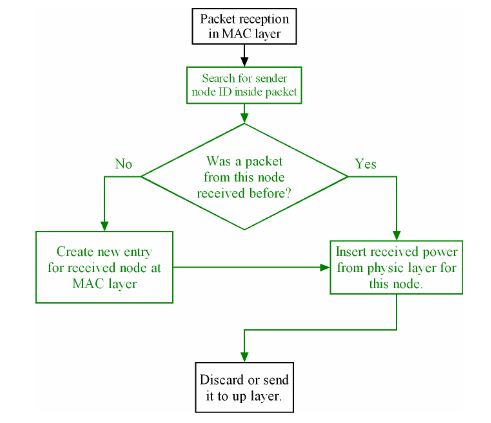
Figure 8: MAC layer at receiver node. A packet is received even when current node is not the destination node
In this master’s thesis project, we implemented an approach that tracks the received signal strength of each neighbouring node in order to know when a neighbouring node is near enough for a successful transmission. If lost packets are due to congestion and high traffic, normal DSR triggers route error but this is counter productive because it adds more. If lost packets is due to low signal quality or misrouted packets, then route error is needed because receiver is not reachable.
SIMULATION RESULTS
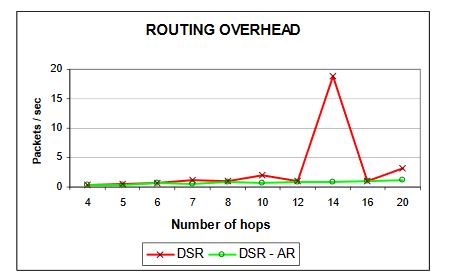
Figure 27:Routing overhead
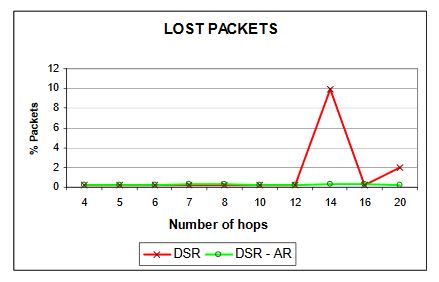
Figure 28:Lost packets
Ns-2 simulated for 14 hops shows a high number of “retry exceed count”, which means that in the MAC layer some packets were not delivered after all possible retransmissions. That explains the higher number of packets lost (figure 28). Because of this, DSR detects a route error and triggers the route maintenance process, which provokes more routing overhead (figure 27), decreasing the overall throughput of the network.
CONCLUSION AND FUTURE WORK
Conclusions
The key issue treated in this master’s thesis project has been the improvement of the throughput and reduction of routing overhead in mobile ad hoc networks using the ns-2 network simulator. We performed several simulations in both static and mobile scenarios with two transport protocols, TCP and UDP, in order to check the adaptability of proposed approach for different contexts. We focused our work on 2 layers; these are MAC 802.11 protocol in the data link layer and DSR protocol in the routing layer.
Future work
Besides the DSR-AR scheme proposed, we have develop ed a new feature with the objective of avoiding disconnections in scenarios with objects that interfere with the communication among nodes. The main idea makes sense in mobility scenarios, for example an office with mobile nodes. Here the connection can be interrupted easily due to furniture obstructing the communication.
If the receiver node is not moving away from the transmitter node, it is possible to avoid disconnection by making an average of the received signals. This new approach makes a prediction based on the last twenty movements and interprets if the receiver node is not reachable anymore.
Source: Karlstad University
Authors: Guillermo Alonso Pequeno | Javier Rocha Rivera