ABSTRACT
Bluetooth Low Energy (BLE) has emerged as one of the most promising technologies to enable the Internet-of-Things (IoT) paradigm. In BLE-based IoT applications, e.g., wearables oriented service applications, the Bluetooth MAC addresses of devices will be swapped for device pairings. The random address technique is adopted to prevent malicious users from tracking the victim’s devices with stationary Bluetooth MAC addresses and accordingly the device privacy can be preserved. However, there exists a tradeoff between privacy and security in the random address technique. That is, when device pairing is launched and one device cannot actually identify another one with addresses, it provides an opportunity for malicious users to break the system security via impersonation attacks. Hence, using random addresses may lead to higher security risks.
In this study, we point out the potential risk of using random address technique and then present critical security requirements for BLE-based IoT applications. To fulfill the claimed requirements, we present a privacy-aware mechanism, which is based on elliptic curve cryptography, for secure communication and access-control among BLE-based IoT objects. Moreover, to ensure the security of smartphone application associated with BLE-based IoT objects, we construct a Smart Contract-based Investigation Report Management framework (SCIRM) which enables smartphone application users to obtain security inspection reports of BLE-based applications of interest with smart contracts.
RELATED WORK
In recent years, researchers have paid a great deal of attention to the development of IoT-based applications with potential security and privacy issues. In 2012, Jara et al. designed a knowledge acquisition and management platform relying on IoT network architecture. The platform focused on the management of personal health, and enabled delivery of healthcare services by virtue of its capabilities to predict health anomalies in real-time and offer feedback to patients. The next year, Berhanu et al. presented an adaptive security process for IoT devices in an e-Health environment, and examined the validation through the study of the impact of antenna orientation on energy consumption.
THE GENERALIZED REQUIREMENTS
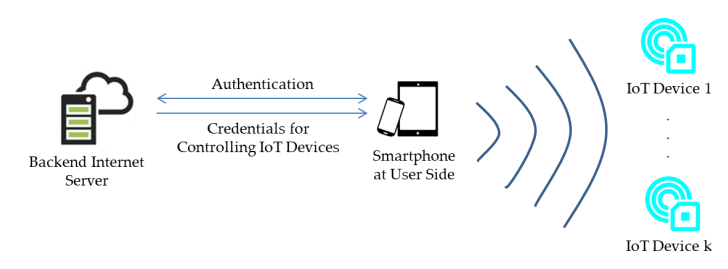
This section provides generalized requirements for BLE-based applications associated with IoT devices. As depicted in Figure 3, users use their smartphones to send requests to an Internet server to verify their identities. The server then sends credentials to the user smartphones to enable the smartphones to connect to nearby IoT devices and to control those devices.
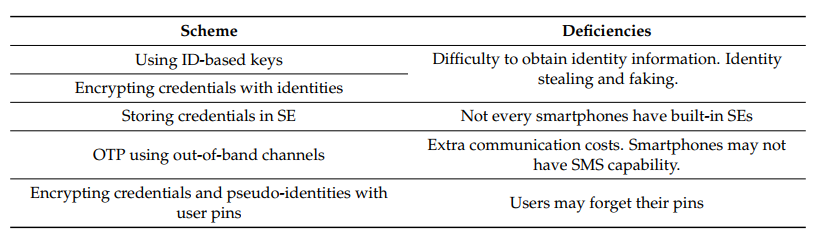
Table 1. List of Schemes to Pair Smartphones to Devices
Table 1 lists possible schemes for IoT devices to identify smartphones. First, after verifying the identities of smartphone users, the Internet server can generate credentials based on the identification information of smartphones. Therefore, an IoT device can restrict access so only the smartphone with the specified identification information can use associated credentials to connect to the device. Similarly, smartphone applications can use smartphone identification information to encrypt credentials for IoT device communication. Then, smartphone applications need to use local identification information to obtain the credentials.
A PRIVACY-AWARE ACCESS-CONTROL MECHANISM FOR BLE-BASED SMART OBJECTS
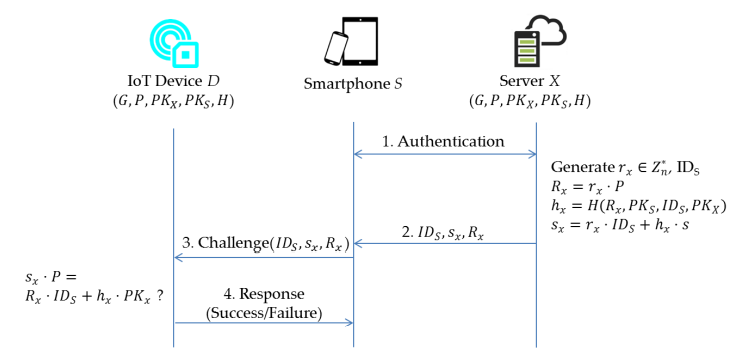
Figure 4. The communication processes of the proposed ECC-based scheme
Verification (Figure 4): first, an authentication between smartphone S and server X is performed. After authenticating the user, the server generates a pseudo-identity IDS for the user. Given params, s and the identity IDS of smartphone S, server X generates a random number rx∈Z∗n, and calculates Rx=rx·P,hx=H(Rx,PKS,IDS,PKX) and sx=rx·IDS+hx· s mod n. Then, server X returns (IDS,sx,Rx) to the smartphone S which soon forwards it to the device D. Then, device D checks the validity of (IDS,sx, Rx) via whether the equation sx·P=Rx·IDS+hx· PKx mod n holds or not.
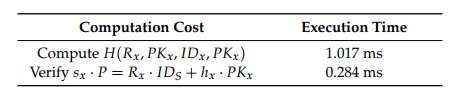
Table 3. Experiment Results at BLE-based IoT Devices
From Table 3, we can see that around 1301ms is required in terms of the execution time for the required computations at BLE-based IoT devices. Note that in the experiment, the smartphone performs only the job of message forwarding, while the server is responsible for the signature generation. Obviously, both of them will not be performance bottlenecks when performing our proposed privacy-aware access-control scheme. Therefore, we only investigate the performance at the IoT device end in which the signature verification is invoked.
SMART CONTRACT-BASED INVESTIGATION REPORT MANAGEMENT FRAMEWORK (SCIRM)
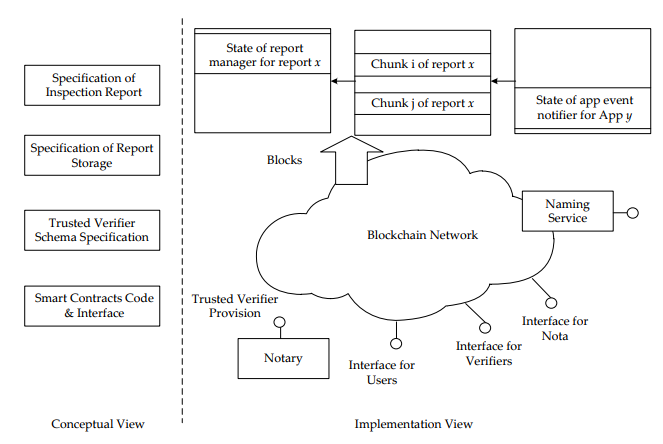
Figure 5 provides an overview of the proposed framework. As depicted in Figure 5, the framework contains two views: the conceptual view and the implementation view. The conceptual view is composed of four major standards:
- The Specification of Inspection Report defines the components of an inspection report as well as the format of each component. In general, an inspection report includes a list of inspection results. Each inspection result is for a security objective. An inspector can describe findings about whether an application comply with a security objective in an inspection result.
- The Specification of Report Storage clarifies how to store an inspection report in the blockchain.
- The Trusted Verifier Schema Specification provides properties required to describe a trusted verifier. In general, users may not know the trustworthy of an inspector and the inspection reports it issued. This study assumes that a notary can provide identities and associated public keys for well-known inspectors. For example, Taiwan has the Accreditation Program for Mobile Application Basic Security Evaluation Laboratories. The Taiwan Accreditation Foundation lists information about the accredited laboratories on its Web pages. Therefore, we can simply append block chain account identities and associated public keys of the laboratories.
- The standard API and the associated smart contract for report management.
As depicted in Figure 8, when a verifier wishes to upload an inspection report for an application, the verifier will first split the report into several chunks and submit transactions containing the chunks to the block chain network. The verifier then generates a report manager smart contract with application profiles, total chunk number of the report, and the address of the applications event notifier smart contract.
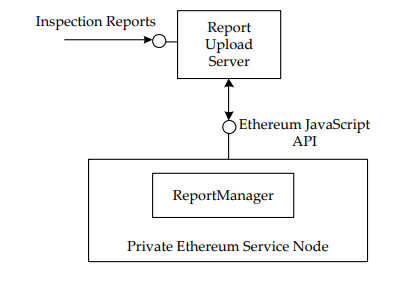
Figure 10. The experimental scenario
To prove the concept of the proposed framework, we have implemented a prototype system and performed simulation experiment. As shown in Figure 10, we use Node.js to implement a Report Upload Server to handle inspection report uploads. In addition, this study launches a private Ethereum network with a single service node. The report manager communicates with the node via the Ethereum JavaScript API.
CONCLUSIONS
In this study, we have introduced a robust security paradigm for BLE-based smart objects in the IoT in which two viewpoints on IoT device security and smartphone applications security, respectively, are the focus. First, we addressed the security impact of adopting BLE random address technique on smartphones to prevent malicious adversary from retrieving smartphones’ physical identification codes.
Three critical security requirements for designing privacy-aware access-control schemes on BLE-based smart objects are thus derived. Then, a privacy-aware access-control scheme adopting a robust ECC-based crypto-module is presented to fulfill the claimed requirements. Second, we demonstrate the SCIRM framework for efficiently managing security inspection reports for the BLE-based applications on smartphones associated with IoT objects. Based on our analysis, the proposed SCIRM framework is secure and practical for application scenarios in real world.
Source: National Dong Hwa University
Authors: Shi-Cho Cha | Kuo-Hui Yeh | Jyun-Fu Chen
>> 60+ Antenna Communication Projects for Engineering Students
>> 200+ IoT Led Engineering Projects for Students