ABSTRACT
The security of the Internet of Things (IoT) is receiving considerable interest as the low power constraints and complexity features of many IoT devices are limiting the use of conventional cryptographic techniques. This article provides an overview of recent research efforts on alternative approaches for securing IoT wireless communications at the physical layer, specifically the key topics of key generation and physical layer encryption. These schemes can be implemented and are lightweight, and thus offer practical solutions for providing effective IoT wireless security. Future research to make IoT-based physical layer security more robust and pervasive is also covered.
WIRELESS TECHNOLOGIES FOR IOT AND THEIR SECURITY COUNTERMEASURES
IoT aims to connect everything together and wireless communication is seen as the best option in order to avoid installation costs while enabling ubiquitous connection. IoT devices are normally tiny, embedded, and battery-powered, and thus communicate with each other through various low power wireless communication technologies. This section introduces several popular wireless technologies, including IEEE 802.15.4 (Zigbee),BLE,IEEE 802.11, and LoRaWAN.
IEEE 802.15.4 defines the physical and MAC layer protocols while Zigbee is based on IEEE 802.15.4 and includes high layer protocols. It runs at an unlicensed industrial, scientific and medical (ISM) 2.4GHz frequency and uses direct sequence spread spectrum (DSSS) as the physical layer modulation. IEEE 802.15.4 is energy efficient and supports a data rate of up to 250kbps, which is quite suitable for applications with limited data exchange requirements. It has been used extensively in wireless sensor networks (WSNs), especially in industrial applications.
PHYSICAL LAYER KEY GENERATION
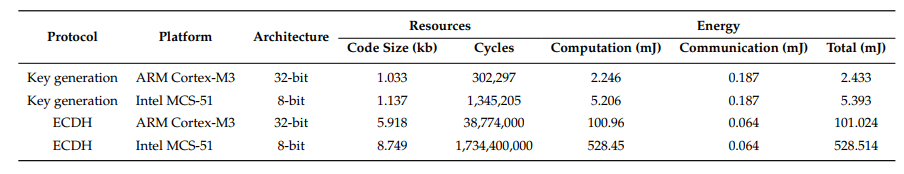
Table 2. Resource and energy consumption comparison between key generation and elliptic curves Diffie–Hellman (ECDH)
As shown in Table 2, taking the implementation in a 32-bit ARM processor as an example, the ECDH requires 5.73 times more code, 128.26 times more cycles, and consumes 41.52 times more energy, than that of the key generation protocol, respectively. Therefore, key generation from wireless channels is extremely suitable for low-cost IoT devices.
PHYSICAL LAYER ENCRYPTION
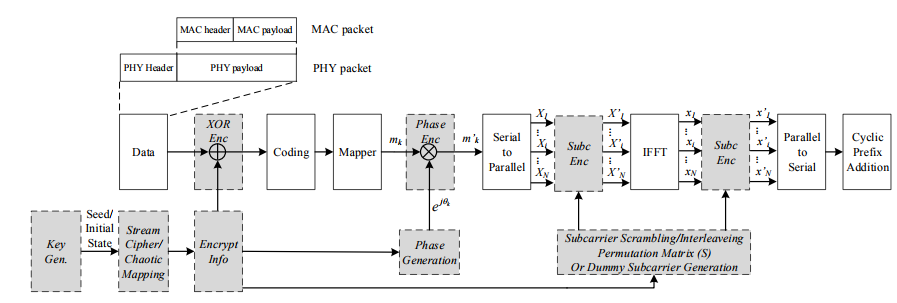
Figure 4. Physical layer encryption schemes in orthogonal frequency-division multiplexing (OFDM). Gray modules are added for encryption
The data payload undergoes several physical layer modulation stages, such as channel coding, mapping, inverse fast Fourier transform (IFFT) operation (for OFDM systems), etc. PLE can be applied by encrypting the data flow in these physical layer modulation stages. Some PLE schemes applicable for OFDM systems are shown in Figure 4, including XOR encryption, phase encryption, and OFDM subcarriers encryption.
The user first generates the encryption information using the output of stream cipher or chaotic mapping. Based on the adopted encryption scheme, the encryption information is used to calculate phase rotation, dummy subcarrier locations, or subcarrier scrambling/interleaving permutation, etc., which is then used to protect the corresponding modulation stage.
FUTURE WORK SUGGESTIONS
Although there have been prototypes/demonstrations of the above physical layer-based security countermeasures, research is still needed to make these schemes more robust and pervasive. In this section, we suggest some future research directions in securing the IoT from the physical layer.
- Physical Layer Key Generation
- Physical Layer Encryption
Physical Layer Key Generation
Most current commercial platforms work in half-duplex mode, and the keying nodes have to measure the channel alternately in different time instances. Key generation in this setting is only applicable to slow fading channels in order to get highly correlated measurements between users. Therefore, key generation in fast fading channels is very challenging, which limits its application, e.g., in vehicular communications.
Physical Layer Encryption
PLE applies encryption at the physical layer, and entails additional operations and hardware resources. No hardware implementation for PLE schemes has been reported except for those in. The additional operations will introduce latency in the critical path and may not meet the timing requirements of the current MAC protocol. Therefore, a cross-layer design between the physical and MAC layer is necessary.
CONCLUSIONS
This article has provided an overview of securing wireless communications of IoT applications from the physical layer. We have introduced two security techniques, namely, physical layer key generation and physical layer encryption. For each, we have discussed their features and applications by a special consideration of IoT devices’ low power and low-cost features. The remaining challenges of how to make these schemes more robust and pervasive have also been proposed. Unlike previous work, this article has focused on practical prototypes/implementations, thus offering insights into their applications in the IoT to enhance wireless security.
Source: Queens University Belfast
Authors: Junqing Zhang | Trung Q.Duong | Roger Woods | Alan Marshall
>> Top Sensor based IoT Projects for Engineering Students
>> IoT based Embedded Projects for Engineering Students with Free PDF Downloads
>> Latest 50+ IoT based Security Projects for Engineering Students
>> Wireless Sensor Networks Projects Abstract for Final Year Students