ABSTRACT
Wireless sensor networks (WSNs) provide noteworthy benefits over traditional approaches for several applications, including smart homes, healthcare, environmental monitoring, and homeland security. WSNs are integrated with the Internet Protocol (IP) to develop the Internet of Things (IoT) for connecting everyday life objects to the internet. Hence, major challenges of WSNs include: (i) how to efficiently utilize small size and low-power nodes to implement security during data transmission among several sensor nodes; (ii) how to resolve security issues associated with the harsh and complex environmental conditions during data transmission over a long coverage range. In this study, a secure IoT-based smart home automation system was developed.
To facilitate energy-efficient data encryption, a method namely Triangle Based Security Algorithm (TBSA) based on efficient key generation mechanism was proposed. The proposed TBSA in integration of the low power Wi-Fi were included in WSNs with the Internet to develop a novel IoT-based smart home which could provide secure data transmission among several associated sensor nodes in the network over a long converge range. The developed IoT based system has outstanding performance by fulfilling all the necessary security requirements. The experimental results showed that the proposed TBSA algorithm consumed less energy in comparison with some existing methods.
RELATED WORK
Recently, IoT has been applied in numerous applications including smart home monitoring systems for assisted living to predict the wellness of residents through the monitoring of several home appliances, building management framework to support energy-saving applications, and human activity patterns monitoring among others. As the Internet communications infrastructure develops to include sensing objects, suitable mechanisms are needed to secure communications with such entities, in the context of IoT applications.
In real world IoT applications, security threats and attacks are becoming a major issue with respect to data transmission. Hence, it is extremely crucial that the IoT based system should include security mechanism that could resist possible security threats and attacks in the form of data modification, impersonation, and eavesdropping, among others.
SECURITY REQUIREMENTS IN IOT BASED HOME AUTOMATION USING WSNS
Security is one of the most imperative aspects of any system. People have distinct perceptions concerning security and therefore it is defined in numerous ways. Generally, security helps protect the entire system from external as well as internal risks. At present, WSNs are useful platforms in IoT-based smart home applications, and data transmission in these networks is usually done through wireless medium. This could cause several severe attacks to the networks as well as pose security threats to WSNs. This section describes the main requirements for implementing security in IoT based applications.
METHOD AND IMPLEMENTATION
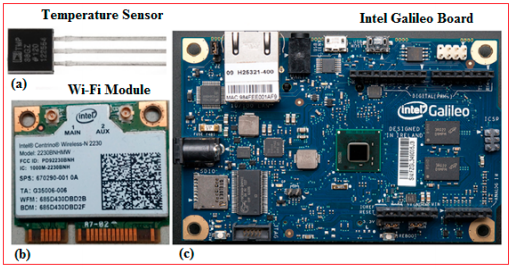
Figure 1. The components for the sensor node
(a) temperature Sensor; (b) Wi-Fi Module (N-2320); (c) Intel Galileo Board.
In this study, WSN was developed at School of Engineering and Advanced Technology (SEAT), Massey University, Palmerston North, New Zealand. The TMP36 temperature sensors were used for capturing environmental temperature which served as the dataset in the study. The components used to build the sensor nodes are shown in Figure 1.
The temperature sensor is presented in Figure 1a, and Figure 1b shows the Wi-Fi module (Intel Centrino Wireless N-2230) which were both integrated on an Intel Galileo based microcontroller board as demonstrated in Figure 1c. The Galileo board includes a 32-bit Intel Pentium-class system mounted on a chip that contains an Arduino Software Development Environment (IDE), together with an Intel processor for fast processing of data.
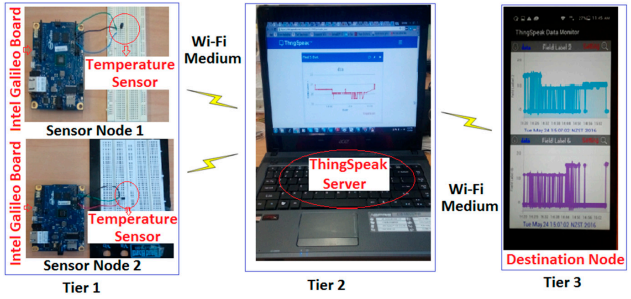
The architecture of WSNs including three tiers for data transmission between the source and destination nodes is shown in Figure 2. In tier 1, the sensor nodes were designed to collect data by using Wi-Fi as a wireless medium, the sensed data is then stored on the server in tier 2. In this study, a ThingSpeak server was used to store the recorded data. Finally in tier 3, the stored data was transmitted to the destination node after proper authentication.
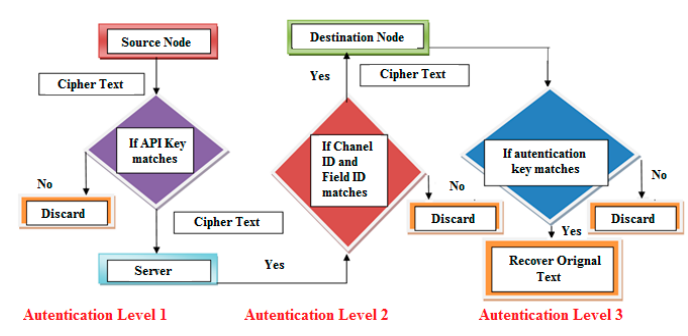
Figure 6. Three-levels of network security for IoT-based systems
The IoT-based platform was implemented on the basis of the proposed security algorithm that provides network authentication at three different levels as shown in Figure 6. Authentication level 1 includes security of data transmitted from the source to the server, and if KAPI does not match at the source node, communication will not be initiated. In our proposed system, the server validates the source node by verifying the onetime alias identity KAPI and the track sequence number Ts, where only a valid sensor node can start communication with the server (authentication).
EXPERIMENT RESULTS AND DISCUSSION
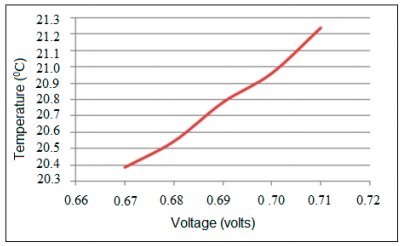
Figure 8. Temperature values against corresponding voltage values
The actual output from TMP36 is in ADC; the ADC value should be converted into the correct voltage (VTMP). The ADC value (ADCoutput) is initially compared with the reference voltage of 5V and then the characteristics of the TMP36 are used to obtain the temperature (T) as represented by the Equation. The linear relationship between voltage and temperature is shown in Figure 8.
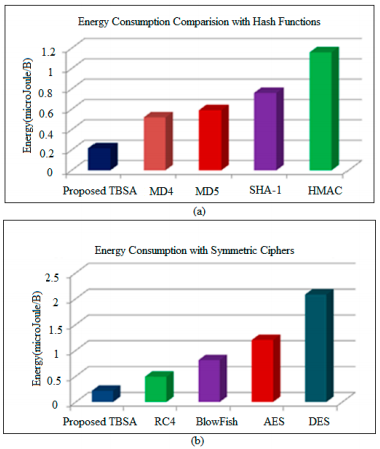
Figure 11. Energy consumption comparison of proposed TBSA
(a) with Hash Functions; (b) with Symmetric Cipher.
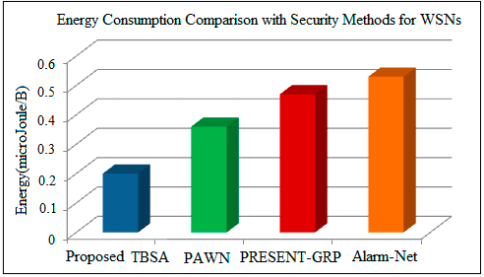
Figure 12. Energy consumption comparison of proposed TBSA with security mechanisms developed for WSNs
It has been observed from Figures 11 and 12 that the proposed TBSA algorithm requires less energy for its implementation in comparison with traditional security methods. As a simple and efficient key generation mechanism is used in TBSA, therefore less energy is consumed. Therefore, the proposed secure IoT-based home automation incorporates the proposed TBSA and low power Wi-Fi in WSNs with internet for providing efficient and secure data transmission among several nodes at wide coverage range.
CONCLUSIONS
This paper proposed secured IoT-based home automation applications using WSNs. In WSNs, because of the limited computational power of sensor nodes, an efficient security mechanism based on effective key generation mechanism which could accomplish all major data security requirements and consumes less processing time for data encryption is well needed. In this study a security algorithm, namely TBSA, based on a simple and efficient key generation procedure is developed.
The proposed IoT integrates low power Wi-Fi and the proposed TBSA in WSNs with internet to provide additional benefits of increased coverage range and capability of supporting large number of sensor nodes due to usage of low power Wi-Fi module; it also consumes less processing time for data encryption because of the utilization of the proposed TBSA algorithm. The experimental results obtained from the hardware implementation have elaborated that the proposed algorithm TBSA is more energy-efficient for data encryption than all compared approaches. Furthermore, it has been verified in this study that developed IoT platform fulfills all major security requirements including network security (secure localization, non-repudiation, availability, access control, trustworthiness and authentication) and data security (confidentiality, privacy, integrity, and data freshness).
In near future, proposed IoT platform will be implemented for different applications such as medical monitoring and emergency response, agriculture, healthcare, energy management, and industrial automation. Additionally, we will develop an efficient biometric-based security algorithm based on Heart Rate Variability (HRV) to secure modern healthcare system using Wireless Body Sensor Networks (WBSNs). The time-domain parameters of HRV such as Standard Deviation of NN interval (SDNN) and Root-Mean Squared of the Successive Differences (RMSSD) along with TBSA will be used for key generation or entity identifications in WBSNs.
Source: Shenzhen University
Authors: Sandeep Pirbhulal | Heye Zhang | Md Eshrat E Alahi | Hemant Ghayvat | Subhas Chandra Mukhopadhyay | Yuan-Ting Zhang | Wanqing Wu
>> Latest IoT based Automation Projects for Engineering Students
>> IoT Software Projects for Final Year Students
>> More Wireless Projects using Arduino for Final Year Students
>> Wireless Sensor Networks Projects Abstract for Final Year Students