ABSTRACT
To counteract current trends in network malware, distributed solutions have been developed that harness the power of collaborative end-host sensors. While these systems greatly increase the ability to defend against attack, this comes at the cost of complexity due to the coordination of distributed hosts across the dynamic network. Many previous solutions for distributed membership maintenance are agnostic to network conditions and have high overhead, making them less than ideal in the dynamic enterprise environment.
In this work, we propose a network-aware, distributed membership protocol, CLUSTER, which improves the performance of the overlay system by biasing neighbor selection towards beneficial nodes based on multiple system metrics and network social patterns (of devices and their users). We provide an extensible method for aggregating and comparing multiple, possibly unrelated metrics. We demonstrate the effectiveness and utility of our protocol through simulation using real-world data and topologies. As part of our results, we highlight our analysis of node churn statistics, offering a new distribution to accurately model enterprise churn.
DDI SYSTEM MODEL
A simplified depiction of DDI is shown in Figure 1. Hosts participating in the DDI system are embued with anomaly-detecting sensors producing measurement data known as local detectors and aggregating sensors that consume this data to supply inference across time, sensors, and/or machines known as global detectors. Along with these two types of detectors, the DDI end-node architecture also includes a back-end agent that supplies membership tracking of available DDI nodes, a messaging library to support gossip-style communication between nodes, and the capability to track the performance of components in the system.
EXPERIMENTAL METHODOLOGY
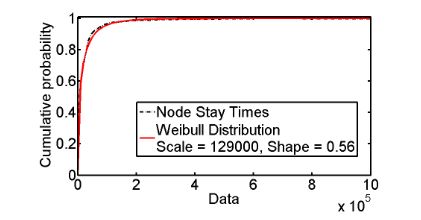
Fig. 2. Distribution of Actual Node Connectivity
However, contrary to popular assumptions, we find that the Pareto distribution that is often used to model node connectivity does not accurately fit our enterprise data. We find, irrespective of the number of weeks, that node connectivity can be accurately represented by a Weibull distribution, seen in Figure 2, with the scale parameter η = 12900, the shape parameter β = 0.56, and the location parameter γ = 0. This implies other simulations can accurately model the social patterns of end-nodes in a large enterprise network by using a Weibull distribution instead of the Pareto distribution for node connectivity.
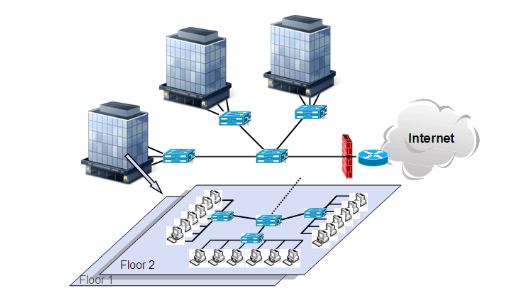
Fig. 3. Example of an enterprise campus network
We also utilize the enterprise topology shown in Figure 3, which is based on the construction of a typical Intel enterprise campus network. Inside the enterprise network, there are one or more buildings linked by a networking device (e.g., switch). Inside each of the buildings are multiple networked floors, with each floor containing several sub-networks. These sub-networks consist of a set of end-user nodes, each running the DDI system. Our simulation topology consists of 3 buildings with 2 floors per building.
RELATED WORK
In this section, we provide an overview of the previous research in two areas related to our work: membership protocols and modeling node behavior in distributed systems.Recently, there has been increasing interest in membership protocols for unstructured distributed systems. SCAMP is a self-organizing peer-to-peer membership service which provides each node in a system of size N with a membership view of the network with a size O(log N).
CONCLUSIONS
In this paper, we present a network-aware distributed membership protocol, CLUSTER, that offers significant performance improvements over other state-of-the-art membership management schemes. Moreover, CLUSTER improves the performance of collaborative defense algorithms, such as DDI, which depend on robust, scalable membership tracking in a dynamic operational setting.
CLUSTER biases membership decisions toward nodes with desirable attributes as a consequence of using the data gained from observing multiple system metrics and network social patterns (of devices and their users). Additionally, we design an extensible method for aggregating multiple, possibly unrelated metrics into a single Proximity function and show its utility in simulation.
Using real-world traffic patterns, topologies, and churn rates, we demonstrate through simulations that our protocol, at minimum, is able to decrease the infection rate of the system by 24% and the false positive rate by 58%, while reducing the overhead by 2 orders of magnitude. Finally, our analysis of node churn in the enterprise network unexpectedly reveals that a Weibull distribution can be used to accurately simulate enterprise traffic patterns when actual data is not available.
Source: Purdue University
Authors: David Zage | Carl Livadas | Eve M.Schooler