ABSTRACT
Bluetooth is one of the most popular technologies in the world in the new century. Meanwhile it attracts attackers to develop new worm and malicious code attacking Bluetooth wireless network. So far the growth of mobile malicious code is very fast and they have become a great potential threat to our society. In this thesis, we study Bluetooth worm in Mobile Wireless Network.
Firstly we investigate the Bluetooth technology and several previously appeared Bluetooth worms, e.g. “Caribe”, ”Comwar”, and we find the infection cycle of a Bluetooth worm. Next, we develop a new simulator, Bluetooth Worm simulator (BTWS), which simulates Bluetooth worm behaviors in Mobile wireless networks. Through analyzing the result, we find i) In ideal environment the mobility of Bluetooth device can improve the worm’s propagation speed, but combining mobility and inquiry time issue would cause a Bluetooth worm to slow down its propagation under certain situation.
ii) The number of initially infected Bluetooth devices mostly affects the beginning propagation speed of a worm, and energy issue can be ignored because the new technology can let Bluetooth device keeping work for a long time. iii) Co-channel interference and setting up monitoring system in public place can improve the security of Bluetooth wireless network.
RELATED WORK
Researcher had already done a lot of work on Internet worm including wire and wireless network, and most of them focus on analyzing, modeling and simulating. But for Bluetooth wireless network, there are few papers, especially on worm propagation behaviors analyzing. Yan et al propose a baseline worm model to analyze the speed of Bluetooth worm propagation. Yan also use the radio propagation model to calculate signal attenuation.
SIMULATION
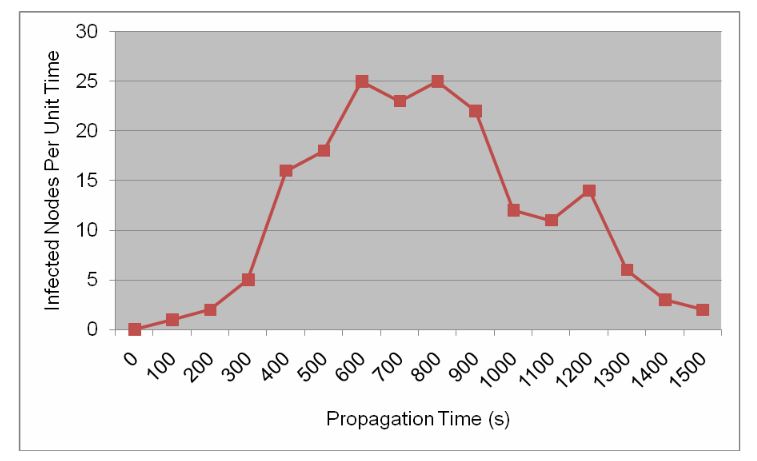
Figure 5: Bluetooth worm propagation speed per unit time
In Figure 5, the two sides, the beginning and the end of worm propagation, the spreading speed is low because there are few infected node at the start time and at the end it is difficult to find un-infected neighbors. The important phase is the middle of worm propagation, and the infected nodes significantly replicate themselves to attack vulnerabilities.
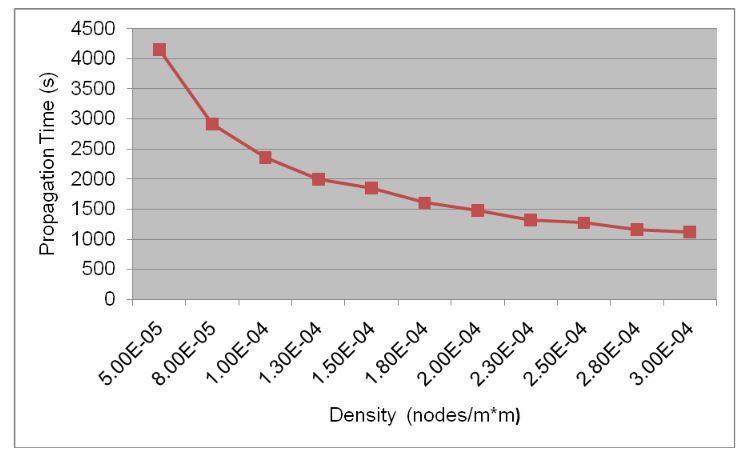
Figure 8: Propagation Time in Different Density
Figure 8 presents a curve between the propagation time and density of the network. Obviously, with increasing the density of the network, in other words, increasing the number of nodes, worm spreading speed is faster and more nodes are infected. When only 50 nodes are in 1000 X 1000 square areas, the density is 5.00E-5.
DEFENSE
Product developers that use Bluetooth wireless technology in their products have several options to implement security issues. There are three modes of security for Bluetooth access between two devices.
Security Mode 1: non-secure
Security Mode 2: service level enforced
security Security Mode 3: link level enforced security
CONCLUSION
Computer worm spread by Bluetooth technology still is a new way in the wireless network, and so far it does not bring the huge damage for wireless networks. Since all Bluetooth worms need be activated by a manual operation, it cannot spread rapidly. However, Bluetooth technology will be growth quickly in order to communicate in larger range, to transfer bigger size package and more rapidly, and smart phones will become a mobile micro device with full computer’s functions. Those new techniques will boost the Bluetooth worm propagation in wireless networks.
To reduce the Bluetooth worm damage, even to predict the Bluetooth worm, this thesis studies its behaviors based on new simulator–BTWS. The mobility of Bluetooth-enabled devices in Mobile wireless network is the primary effect of the worm spreading, and if attackers control their speed at 1 or 2 m/s so as to achieve the maximum worm propagation. The Inquiry time is another key feature of Bluetooth technology, and it determines whether or not the worm can infect vulnerable devices.
If the new-generation Bluetooth technology can significant reduce the inquiry time, it will be easy for Bluetooth devices to communicate to each other, but it is also a disaster for the wireless network security. In the large wide wireless environment, attackers could change its location in order to spread the worm quickly. For network security issue, it is hard for security engineer to find the source of the worm due to its mobility. In the future, we can build a worm propagation model to further study its behavior in order to improve the defense system.
Source: University of Central Florida
Authors: Haiou Xiang
>> More Wireless Bluetooth Projects for Final Year Students