ABSTRACT
Multi-hop wireless networks rely on node cooperation to provide unicast and multicast services. The multi-hop communication offers increased coverage for such services, but also makes them more vulnerable to insider (or Byzantine) attacks coming from compromised nodes that behave arbitrarily to disrupt the network.
In this work we identify vulnerabilities of on-demand multicast routing protocols for multi-hop wireless networks and discuss the challenges encountered in designing mechanisms to defend against them. We propose BSMR, a novel secure multicast routing protocol that withstands insider attacks from colluding adversaries. Our protocol is a software-based solution and does not require additional or specialized hardware. We present simulation results which demonstrate that BSMR effectively mitigates the identified attacks.
RELATED WORK
Significant work addresses vulnerabilities of unicast routing protocols in wireless networks. Several secure routing protocols resilient to outside attacks were proposed in the last few years such as Ariadne, SEAD, ARAN, and the work. Wireless specific attacks such as flood rushing and wormhole were recently identified and studied. RAP prevents the rushing attack by waiting for several flood requests and then randomly selecting one to forward, rather than always forwarding only the first one.
NETWORK AND SYSTEM MODEL
We consider a multi-hop wireless network where nodes participate in the data forwarding process for other nodes. We assume that the wireless channel is symmetric. All nodes have the same transmitting power and consequently the same transmission range. The receiving range of a node is identical to its transmission range. Nodes are not required to be equipped with additional hardware such as GPS receivers or tightly synchronized clocks. Also, nodes are not required to be tamper resistant: If an attacker compromises a node, it can extract all key material, data or code stored on that node.
ATTACKS AGAINST MULTICAST ROUTING
We assume that nodes may exhibit Byzantine behavior, either alone or colluding with other nodes. Examples of such behavior include: not forwarding packets, injecting, modifying or replaying packets. We refer to any arbitrary action by authenticated nodes resulting in disruption of the routing service as Byzantine behavior, and to such an adversary as a Byzantine adversary.
SECURE MULTICAST ROUTING PROTOCOL
Our protocol ensures that multicast data is delivered from the source to the members of the multicast group, even in the presence of Byzantine attackers, as long as the group members are reachable through non-adversarial paths and a non-adversarial path exists between a new member and a node in the multicast tree. To eliminate a large class of outside attacks we use an authentication framework that ensures only authorized nodes can perform certain operations (e.g., only tree nodes can perform tree operations and only nodes that possess valid group certificates can connect to the corresponding multicast tree).
EXPERIMENTAL RESULTS
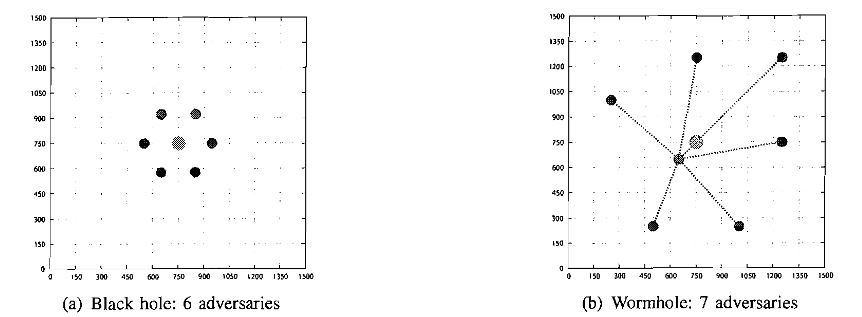
Fig. 4: Examples of strategic adversarial placement for the black hole and wormhole attacks
In Fig. 4, we illustrate the strategic adversarial placement for the black hole attack (in the presence of 6 adversaries) and for the wormhole attack (in the presence of 7 adversaries). To study the influence of whether the adversaries explicitly join the multicast group and the order of joining, we consider two scenarios:
– NJOIN: adversarial nodes do not join the group;
-JOIN: adversarial nodes explicitly join the group before any of the honest members join. The adversaries are considered group members in the formula for PDR.
CONCLUSION
In this paper we have discussed several aspects that make designing attack-resilient multicast routing protocols for multi-hop wireless networks more challenging when compared to their unicast counterpart. A more complex trust model and underlying structure for the routing protocol make solutions tailored for unicast settings not applicable for multicast protocols. In the absence of defense mechanisms, Byzantine attacks can prevent multicast protocols to achieve their design goals.
We have proposed BSMR, a routing protocol which relies on novel general mechanisms to mitigate Byzantine attacks. BSMR identifies and avoids adversarial links based on a reliability metric associated with each link and capturing adversarial behavior. Our experimental results show that BSMR’s strategy is effective against strong insider attacks such as black holes and flood rushing. We believe that this strategy can also be effective against wormhole attacks and defer the experimental validation for future work.
Source: Purdue University
Authors: Reza Curtmola | Cristina Nita-Rotaru