ABSTRACT
Substantial changes have occurred in the Information Technology (IT) sectors and with these changes, the demand for remote access to field sensor information has increased. This allows visualization, monitoring, and control through various electronic devices, such as laptops, tablets, i-Pads, PCs, and cellular phones.
The smart phone is considered as a more reliable, faster and efficient device to access and monitor industrial systems and their corresponding information interfaces anywhere and anytime. This study describes the deployment of a protocol whereby industrial system information can be securely accessed by cellular phones via a Supervisory Control And Data Acquisition (SCADA) server. To achieve the study goals, proprietary protocol interconnectivity with non-proprietary protocols and the usage of interconnectivity services are considered in detail.
They support the visualization of the SCADA system information, and the related operations through smart phones. The intelligent sensors are configured and designated to process real information via cellular phones by employing information exchange services between the proprietary protocol and non-proprietary protocols. SCADA cellular access raises the issue of security flaws. For these challenges, a cryptography-based security method is considered and deployed, and it could be considered as a part of a proprietary protocol. Subsequently, transmission flows from the smart phones through a cellular network.
RELATED WORKS
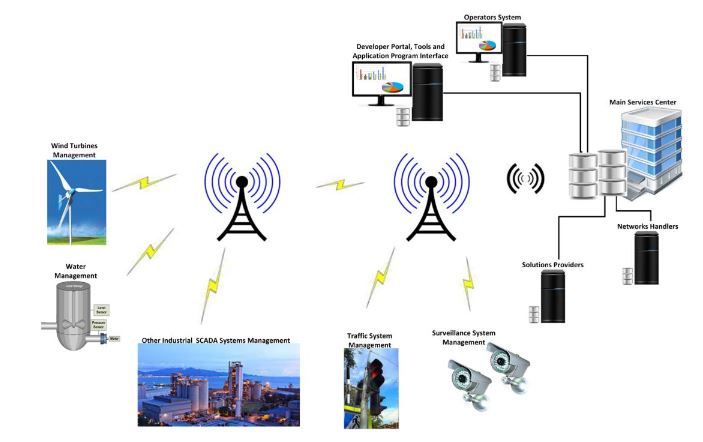
Figure 2. M2M cellular communications
Like the diversity of applications supported by M2M technology, cellular communication is often used in SCADA industrial and manufacturing applications, public and private infrastructure monitoring and management, and agriculture and farm-based applications, and this opens new trends involving remote monitoring and controllers that have been linked with these organizations to provide more reliable, efficient, and optimal solutions that would enhance the organizational performance and profitability. Figure 2 shows the M2M cellular communication for SCADA systems and for other systems.
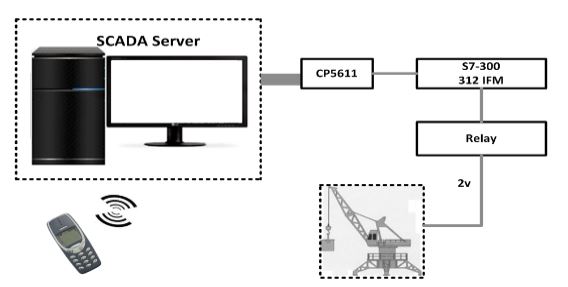
Figure 3. A Mobile-based SCADA application
To access and monitor the crane information using a mobile phone, general packet radio service (GPRS) or wireless application protocol (WAP) transmission were used, which offered significant advantages in increasing the performance without any effect on the SCADA system response-time. In the crane system model (in Figure 3), a PLC (S7 300-312 IFM), I/O card (SM334), a Siemens mobile phone (M50 with 228 Kb storage), and a computer system were employed.
THE DNP3 PROTOCOL AND SCADA SYSTEMS
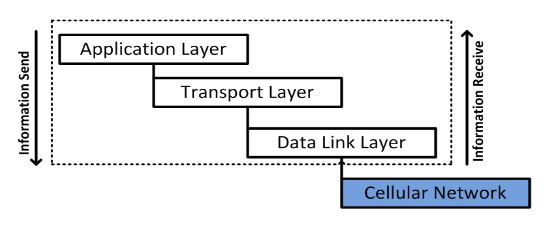
Figure 4. The Basic structure of the SCADA/DNP3 protocol
The FT3 frame format was specified by IEC 870-5-1, and was the fourth format of IEC 870-5 among the other specified formats such as FT1.1, FT1.2 and FT2. The FT3 frame format, as applied in the data link layer, defines the overall link frame size. Its consists of a 10 bytes header, 32 bytes of CRC code, and optionally up to 16 bytes data blocks, while the last block or block 16 contains 10 bytes of data. The maximum size of LPDU is up to 292 bytes as specified by the FT3 frame format. Figure 4 shows the basic structure of the SCADA/DNP3 protocol.
PROPOSED SYSTEM MODEL AND DESIGN
Like traditional computer networks, there is also a requirement to access the remotely located industrial stations from a centralized station. Therefore, the best way is to employ a wireless technology such as a satellite system. Furthermore, the industrial processing system can access mobile phones via cellular networks. As a result, this study proposes a solution that could provide secure industrial access to mobile phones through cellular networks.
PERFORMANCE RESULTS AND DISCUSSION
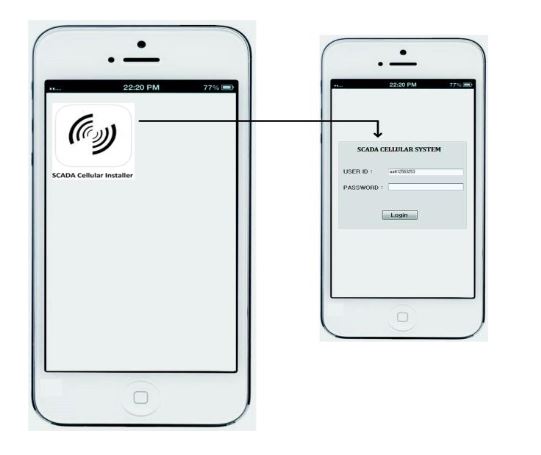
Figure 6: The cellular device secure login
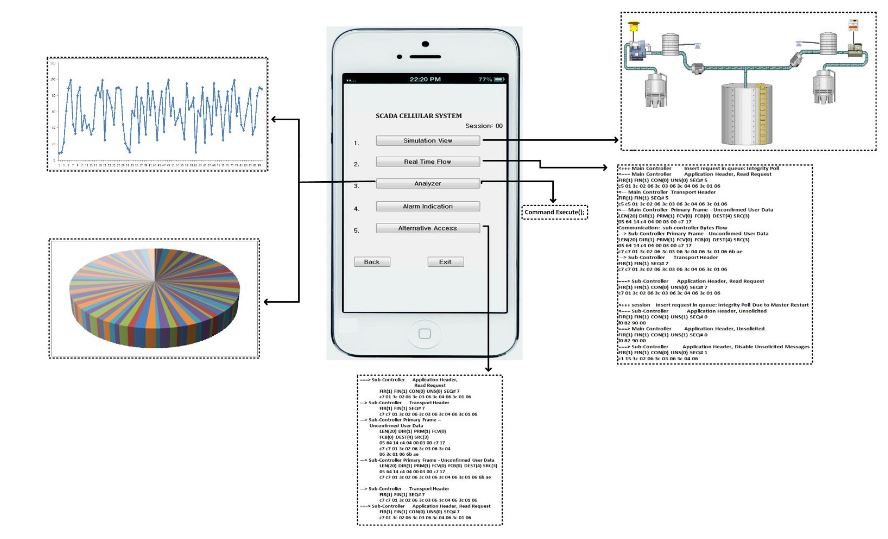
Figure 7. The SCADA cellular interface
In Figure 6, whenever the user logs in via his/her mobile device (i.e., Android or I-Phone), the connection will be directly made to the HTTP server toward the SCADA Web server in the presence of internet access. After the verification process by the main controller, a secured channel access is established and permission is granted to the mobile user, and as a result the mobile user will be able to access the SCADA information, while accessing the interface that has options to access the desired information of the SCADA system. In Figure 7, a user authorized interface is shown in a mobile device, which shows the user enabled options (buttons) to access the desired information of the SCADA system.
CONCLUSIONS
With the technology progress in cellular systems, there are also demands to monitor and to control in real time industrial systems (or SCADA systems) using personal mobile phone(s). Typically, SCADA systems have employed proprietary protocols to carry out their communication between the sensors/devices that are configured and networked as process automation systems. The situations where several sensors that are located at many places must be interconnected to a main controller, are resolved by means of non-proprietary protocols.
Thus, complicated configurations and connectivity services are required to process the proprietary protocols that generate information to and from non-proprietary protocols. As a consequence, in the proposed study, the bytes (or information) of a SCADA system is generated by the employed DNP3 protocol, and the proposed security solution is deployed at the data link layer before transmitting to open networks and/or cellular networks.
A high percentage of security flaws usually occur in the data link layer of the DNP3 protocol due to its operations and connection orientation over physical channels. After passing the frames to a cellular network, these frames are further accessed by cellular devices with monitoring and control facilities that could act as an authorized user of the SCADA cellular system. The authorized cellular device could then view, monitor and control (i.e., provide alarm indications), the SCADA system information according to the premises.
Source: Chonbuk National University
Authors: Aamir Shahzad | Rene Jr. Landry | Malrey Lee | Naixue Xiong | Jongho Lee | Changhoon Lee
>> More Wireless Sensor Networks Projects Abstract for Engineering Students