ABSTRACT
The aim of this paper is to determine the physical proximity of connected things when they are accessed from a smartphone. Links between connected things and mobile communication devices are temporarily created by means of dynamic URLs (uniform resource locators) which may be easily discovered with pervasive short-range radio frequency technologies available on smartphones. In addition, a multi cross domain silent logging mechanism to allow people to interact with their surrounding connected things from their mobile communication devices is presented. The proposed mechanisms are based in web standards technologies, evolving our social network of Internet of Things towards the so-called Web of Things.
ONE-TIME URL MOTIVATION
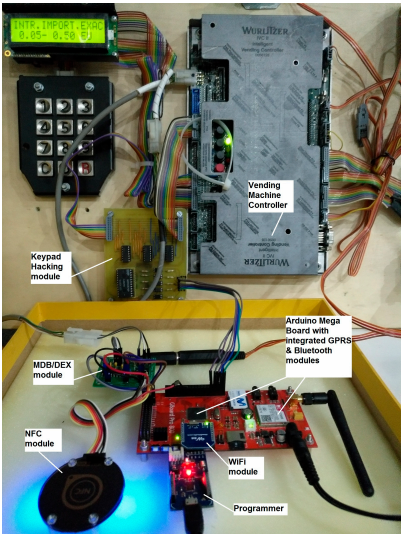
Figure 1. Open hardware prototype
All modules highlighted in Figure 1 are on-the-self products except the MDB/DEX module (multi-drop bus/digital exchange module) and the Keypad Hacking module. These two printed board circuits (PBCs) have been designed for interacting with vending machines in a fully contactless way, i.e., without physically touching the vending machine.
This contactless innovation requires implementing a mechanism to guarantee that the consumer is physically close to the vending machine when products are ordered and dispensed. Collocate the end user and the vending machine, at the time the transaction occurs, is the challenge addressed in this paper. This challenge is solved if the only way to access the digital avatar of the vending machine is through the dynamic URL, and if this URL can only be consumed from the smartphone of an authorized end user.
PROXIMITY SCENARIOS BASED ON SHORT RANGE WIRELESS TECHNOLOGIES
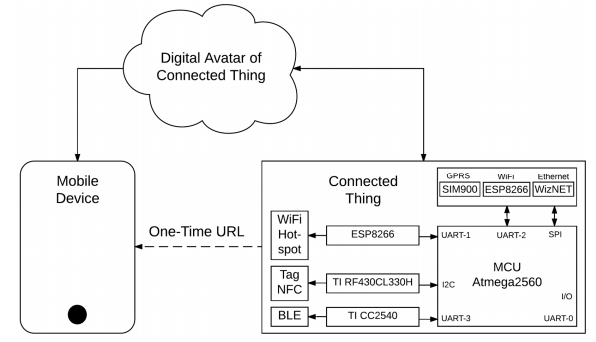
Figure 2. Short range wireless technologies available on smartphones
The aim of this section is to define a user-friendly scenario for mobile users to discover and interact with connected things based on pervasive radio-frequency technologies available on smartphones such as WiFi, Bluetooth or NFC.
In the following subsections, these three short-range radio-frequency technologies are introduced to achieve the same scenario: initiating a mobile browsing session to a landing web page to interact with our surrounding connected things. Figure 2 despites how to add communication modules to a simple 8 bits microcontroller.
DEFINING THE LIVE CYCLE OF DYNAMIC URLS
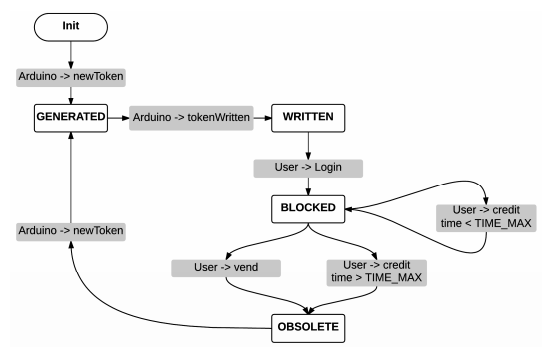
Figure 3. Token life cycle
The main idea behind our research goal is that one-time tokenized URLs, which are announced by connected things, may be used to determine the physical proximity of mobile communication devices. To tokenize a URL is just enough to add a token as parameter to the URL. The Figure 3 depicts the life cycle of the token.
As it is shown, the life cycle of the token follows a state machine workflow in response to events coming either from the connected thing or from the end user mobile device. Furthermore, this approach allows to detect unusual situations and to implement easily corrective actions.
UNDERLYING CLOUD BASED ARCHITECTURE
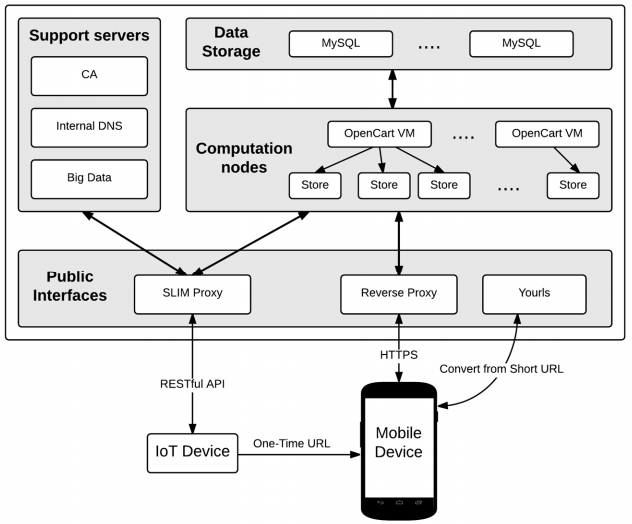
Figure 4. Cloud based architecture
Recently, many research works are interested in combining Cloud Computing and IoT. Figure 4 shows our end-to-end cloud based architecture. The approach is similar to the one followed, but it benefits from the proximity-layer security mechanism presented in this paper.
The overall infrastructure consists of a private cloud, which uses COTS (Commercial Off-The-Shelf) bare-metal servers running OpenStack (https://www.openstack.org/) open source. A detailed description of the main building blocks are presented in the following subsections.
- Slim Proxy
- Reverse Proxy
- URL Shortener
- Other Servers
SECURITY BY DESIGN
1. The username and password are stored in the server encrypted.
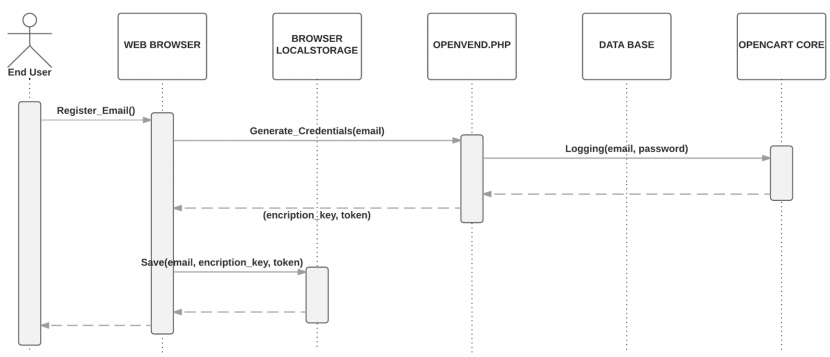
2. The encryption key is stored in the local Storage of the smartphone browser, along with one-time token generated by the server. Figure 5 is a simplified sequence diagram of the registration process which only requires as input a valid end-user email.
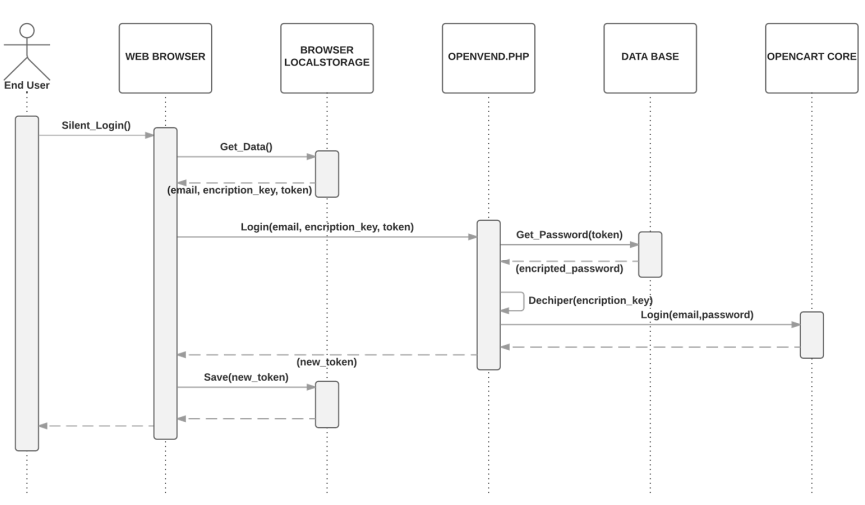
3. Next time the user is going to perform a purchase, a silent login mechanism will retrieve the credentials as show in Figure 6 Both, the encryption key and the token, are sent to the server. The token is checked and if it is correct, the key is used to decrypt the user credentials to log into the server. The encryption key is not kept in the server after it is used.
4. A new token is generated and sent to the user’s smartphone.
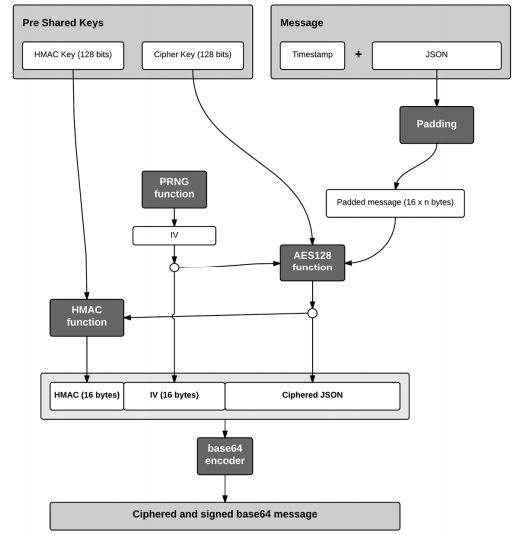
In our API RESTful design, sensitive information is only transmitted in the body of the HTTP requests so it has been decided to encrypt the JSON messages located on the body. After making these decisions, all the steps to encrypt the original message and validate it with the HMAC function are showed in the Figure 7.
CALL FLOW SCENARIO
The scenario starts when the end user provided with a NFC-enabled smartphone taps the NFC module (see Figure 1). The NFC module will launch an interruption to Arduino (see Figure 1) to let him know that someone is reading the short URL. Then, Arduino will query the shopping cart of Opencart (see Figure 4) and wait for the details of the ordered product. Section presents all the communications between Arduino and Opencart. These communications are routed through the SLIM Proxy (see Figure 4).
OPEN HARDWARE PROTOTYPE AND PRELIMINARY BENCHMARKS
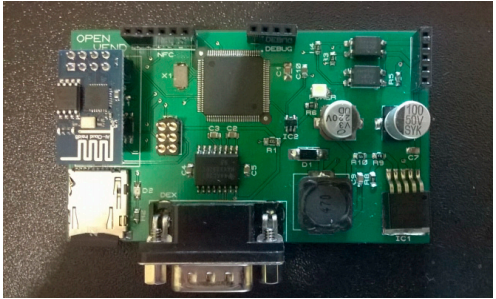
Figure 9. Arduino Mega compatible prototype for vending machines
As reference, Figure 9 shows one of our bespoke Arduino Mega open hardware design. This board is powered by the Multidrop Bus Standard (MDB) interface of the vending machine and it is able to communicate with our cloud solution via WiFi, and to retrieve the one-time URL which is announced via NFC.
CONCLUSIONS
The great potential of the Internet of Things (IoT) is widely known. To unlock its full potential in order to develop IoT solutions it is necessary to bring together connected devices and web standards, conforming the new paradigm of the Web of Things (WoT). The initial motivation of this research was to provide an alternative mobile payment for unattended point of sales just using web standards technologies, without the need to install any native application or mobile wallet. As payment systems deal with sensitive and private data, it makes security to be an integral part of presented work. This paper presents a proximity application layer security mechanism for the WoT applied to unattended point of sales.
It is shown the complete design of the secured proximity layer system to interact with connected things from mobile devices. This approach includes cryptography and tokenization for low-resource devices to ensure its security. Specifically the mechanism to tokenize the URLs, which uniquely identify the thing with its digital avatar. These URLs are broadcasted through pervasive short range radio-frequency technologies available on smartphones. It has also been detailed how the system developed has been integrated as a part of an end-to-end cloud architecture for unattended point of sales to enable proximity mobile payments.
At this point, it is worth it to mention a successful payment mechanism based on tokenized QRs that WeChat has introduced recently in China. Conceptually the presented one-time URLs can be converted to tokenized QRs and be easily displayed in any machine with a screen. Reading these QRs will point consumers to our one-time URLs, so possibilities are endless for disrupting the mobile payment ecosystem of unattended point of sales and by extension to any point of sales. Moreover, other aspects of the security system developed have been analyzed.
These aspects include encryption of the user credentials on mobiles, the verification of multiple origins and a two factor authentication mechanism among others. Standardized secured mechanisms of communication have been used always looking for availability of open source libraries. Finally, some performance benchmarks have been presented to validate the robustness of our open hardware designs and the overall purchasing experience. The next step in this project would be to demonstrate the benefits of our approach in a real case scenario.
Authors: Antonio Solano | Raquel Dormido | Natividad Duro | Víctor González
>> 50+ IoT based Wireless/GSM Projects for Engineering Students
>> IoT based Big Data and Cloud Computing Projects for B.E/B.Tech Students
>> 200+ IoT Led Projects for Engineering Students
>> More Wireless Projects using Arduino for Engineering Students